Updated: Microsoft Exchange Zero-Day (CVE-2022-41040 and CVE-2022-41082)
1664555921055
This article provides information on how you can mitigate the newly discovered Zero-day vulnerabilities in Microsoft Exchange Server using Barracuda WAF-as-a-Service.
These vulnerabilities were published on September 29, 2022, and affect Microsoft Exchange Server 2013, 2016, and 2019. An attacker would need to gain access to the vulnerable system as an authenticated user to exploit these vulnerabilities. CVE-2022-41040 is an SSRF attack that is executed first, to gain access to PowerShell. After that, the attacker can also execute the RCE attack as described in CVE-2022-41082.
Barracuda recommends that mitigation of these vulnerabilities with WAF-as-a-Service using the URL Access & Redirects component to add the following rule;
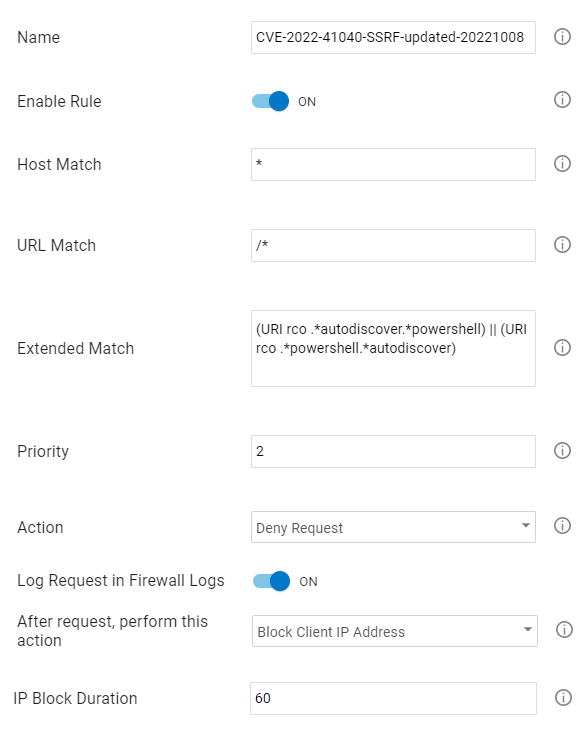
Please note you may need to change the priority of these rules depending on what other rules you already have listed in the URL Access & Redirect component.
For further information on these vulnerabilities please see the Microsoft Advisory here and on Barracuda Campus here.
This article was further updated after new information published by Microsoft on 8th October 2022.
Did you like this update?
![]()
![]()
![]()
Leave your name and email so that we can reply to you (both fields are optional):
