Vulnerability Mapping
1706457600000
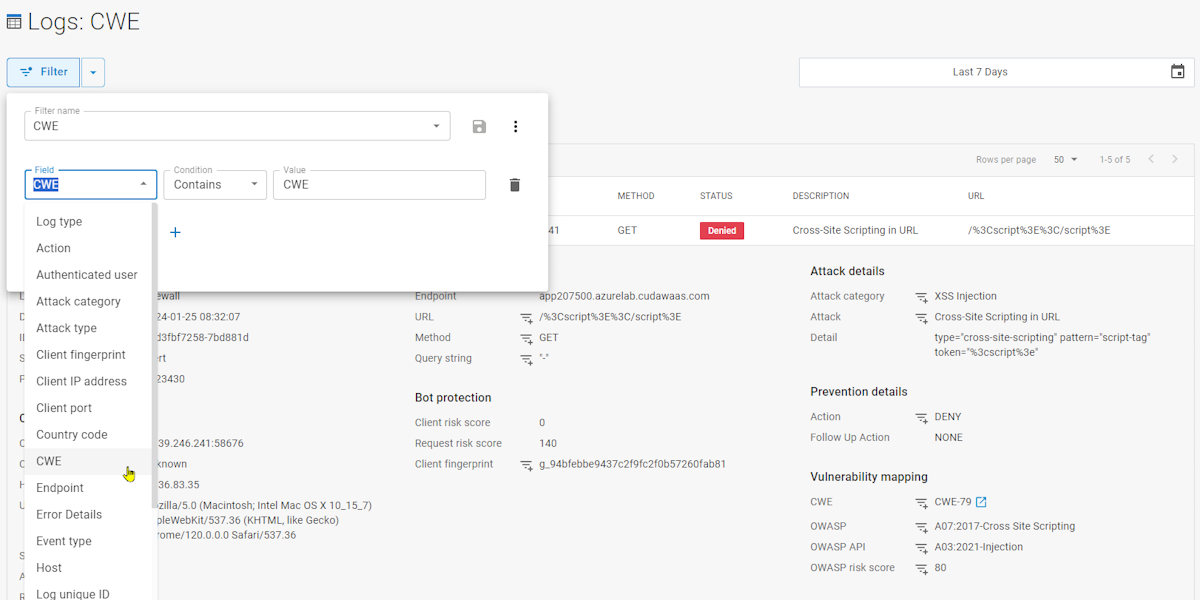
We are pleased to announce that we have released Vulnerability mapping for Common Weakness Enumeration(see above) and several OWASP awareness standards (see below) for log entries in WAF-as-a-Service.
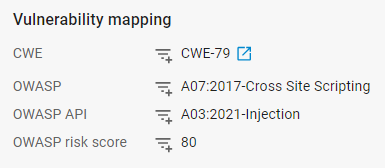
The Vulnerability mapping is dynamic and therefore only shows the mappings that are relevant to the particular log entry. For example we have a log for Cross-Site Scripting in URL (XSS) which has a mapping to CWE-79, the OWASP (Top Ten) and the OWASP API (Top Ten)but no mapping to the OWASP automated threats (see below).
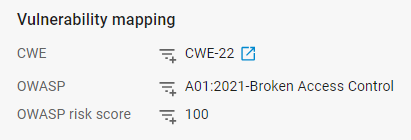
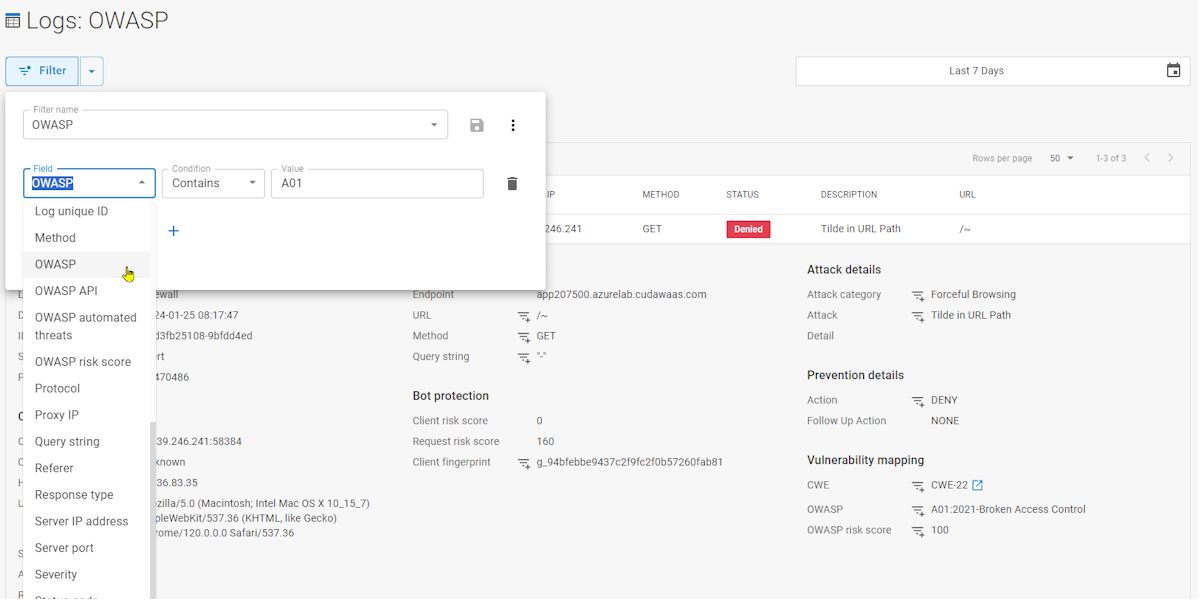
Meanwhile we have another log for a Tilde in URL Path which maps to CWE-22 and the OWASP (Top Ten) but has no mapping to the OWASP API (Top Ten) or the OWASP automated threats (see above).
Finally, there are also OWASP risk scores included where there is an appropriate OWASP mapping.
These mappings should prove invaluable for security policy and risk stakeholders to demonstrate the real attacks that WAF-as-a-Service is protecting their web applications from and therefore allow the stakeholders to calculate the real risk to the business.
We always seek our customers feedback and questions and look forward to finding out how this new feature works for you.
Did you like this update?
![]()
![]()
![]()
Leave your name and email so that we can reply to you (both fields are optional):
